openSafety Stack
openSAFETY protocol stack
The protocol stack was developed by Ixxat together with B&R and is used among others for B&R products, which are already SIL-3 certified. The protocol stack can be downloaded free of charge at Sourceforge.
Features
- Scope of functions based on the current openSAFETY specification
- Modular software structure for the implementation of SN (Safety Slave) and SCM (Safety Master)
- Clearly structured programming interface for connection of the application program
- “C”-source code for use on any target platforms (hardware-independent)
- Independent of operating system – can be run with and without operating system
- Simple connection to a non-safe transport protocol possible via abstraction layer
- Any non-safe transport protocol can be used according to the black channel principle (e.g. POWERLINK, TPC/IP or any other industrial Ethernet Protocol)
- Multi-instancibility allows simple creation of safety domain gateways
- Reference portation for Intel XScale (IXP420) and Atmel ARM7 (AT91SAM7S64) for GNU C-Compilers
- Designed for use in SIL-3 devices
How it works
Hardware concepts for openSAFETY
The Safety Integrity Level (SIL) that can be achieved with the openSAFETY software mainly depends on the hardware architecture used. The openSAFETY software was created for use in SIL-3 devices. To meet the requirements of SIL-1, it is sufficient for example to use one single Safety Controller (SC) that carries out the safe application and the openSAFETY stack. To achieve SIL-3, the Safety Controller must also be designed as redundant.
Overview of functions
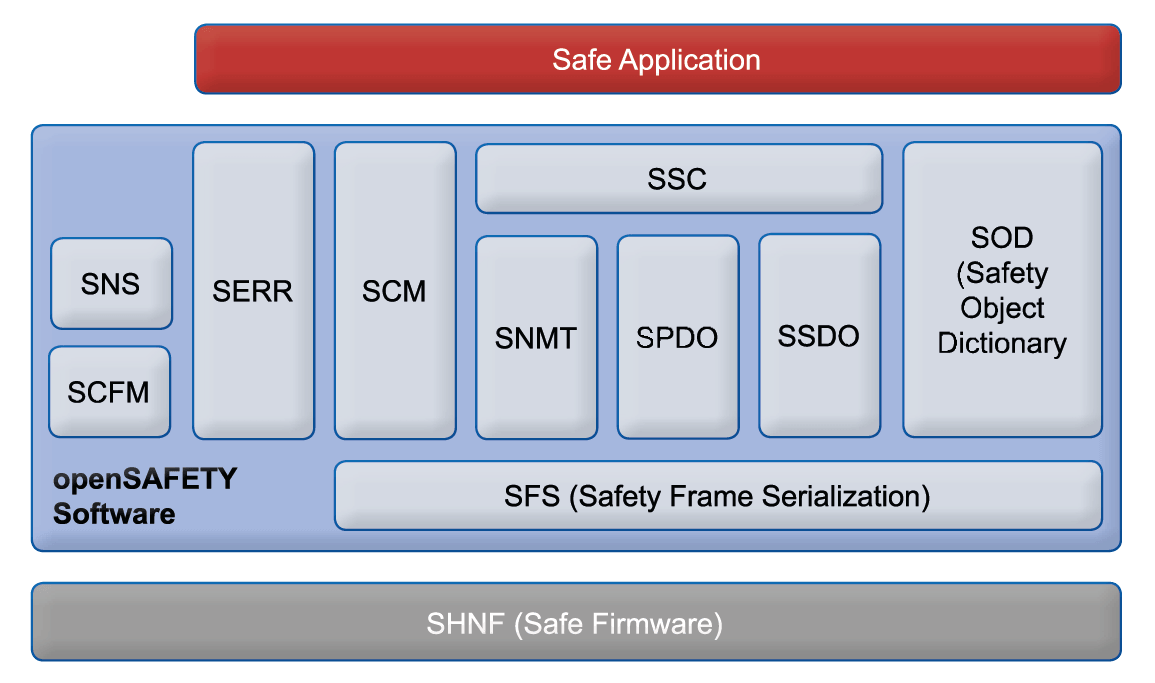
With its function modules, the openSAFETY software enables the execution of all communication and back-up mechanisms necessary for openSAFETY. This includes the provision of a Safe Object Directory (SOD), Safe Process Data (SPDO) and Safe Service Data (SSDO) as well as time and CRC monitoring of the data packages.
Zipping and unzipping of the openSAFETY frames in the transmission messages of the non-safe transmission protocol is carried out by the functions of the hardware-level firmware (SHNF) provided by the user. The inputs and outputs of the openSAFETY device must also be controlled by a special safety application. The SOD of the openSAFETY software is used as the data interface to the safety application.
- SSC: Safety Stack Control: control of the openSAFETY software such as stack initialisation
- SNMT: Safety Network Management: transmission, reception, processing of management commands; distribution of the safety addresses
- SCM: Safety Configuration Manager: configuration, verification and monitoring of safety nodes
- SPDO: Safety Process Data Objects: cyclic exchange of process data and verification of time synchronization
- SSDO: Safety Service Data Objects: server/client communication to access the object directory via the network
- SOD: Safety Object Dictionary: access to the Safety Object Directory
- SFS: Safety Frame Serialization: serialization and deserialization of the safety frames
- SNS: Safety Node State: management of the operating states of the safety nodes
- SERR: Safety Error Handling: logging of stack-internal errors
- SCFM: Safety Control Flow Monitoring: monitoring of the correct program flow in accordance with SIL-3
Hardware and software development services
As development partner we support you at the implementation and portation of openSAFETY at the development of safety applications and safety hardware as well as at the certification. At this, you can benefit from our comprehensive openSAFETY know-how and our competence in the development of safety hardware and software.